Professional cycling has, in its recent history, been prone to a shocking variety of cheating methods and dirty tricks. Performance-enhancing drugs. Tacks strewn on race courses. Even stealthy motors hidden inside of wheel hubs.
Now, for those who fail to download a software patch for their gear shifters—yes, bike components now get software updates—there may be hacker saboteurs to contend with, too.

The trick would, the researchers say, easily be enough to hamper a rival on a climb or, if timed to certain intense moments of a race, even cause dangerous instability. “The capability is full control of the gears. Imagine you're going uphill on a Tour de France stage: If someone shifts your bike from an easy gear to a hard one, you're going to lose time,” says Earlence Fernandes, an assistant professor at UCSD’s Computer Science and Engineering department. “Or if someone is sprinting in the big chain ring and you move it to the small one, you can totally crash a person's bike like that.”
Here's a video demonstration of the researchers’ hacking technique:
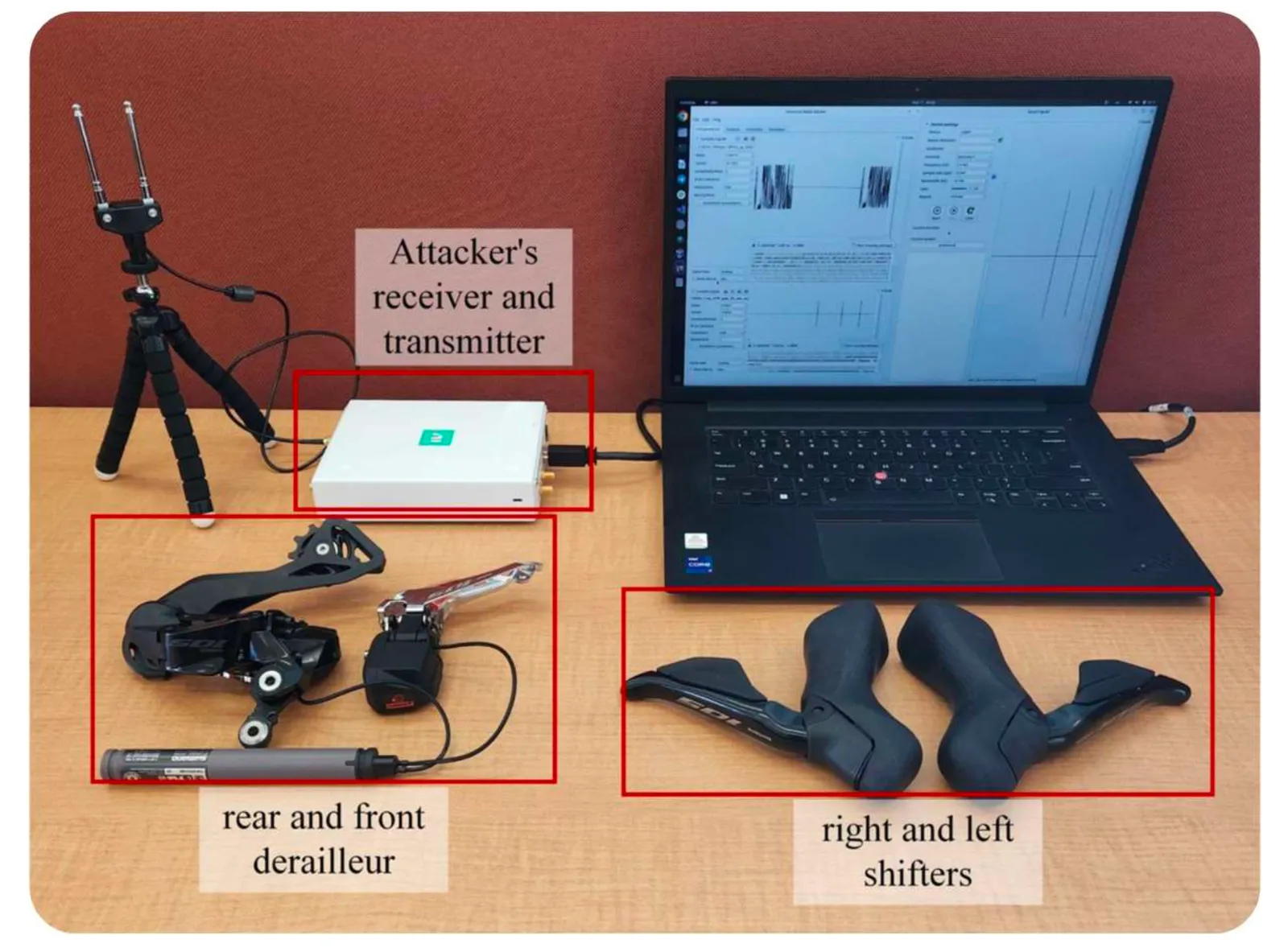
The researchers' technique exploits the increasingly electronic nature of modern high-end bicycles, which now have digital components like power meters, wireless control of fork suspensions, and wireless shifters. “Modern bicycles are cyber-physical systems,” the researchers note in their Usenix paper. Almost all professional cyclists now use electronic shifters, which respond to digital signals from shifter controls on the bike's handlebars to move a bicycle's chain from gear to gear, generally more reliably than mechanical shifting systems. In recent years, those wired electronic shifters have transitioned again to wireless versions that pair via Bluetooth, such as the popular Di2 wireless shifters sold by the Japanese cycling component firm Shimano, which the researchers focused on.


 Loading comments...
Loading comments...
